Proxy Warfare through Cyber Space: Lessons for Border Security from Ukraine and Israel Affairs
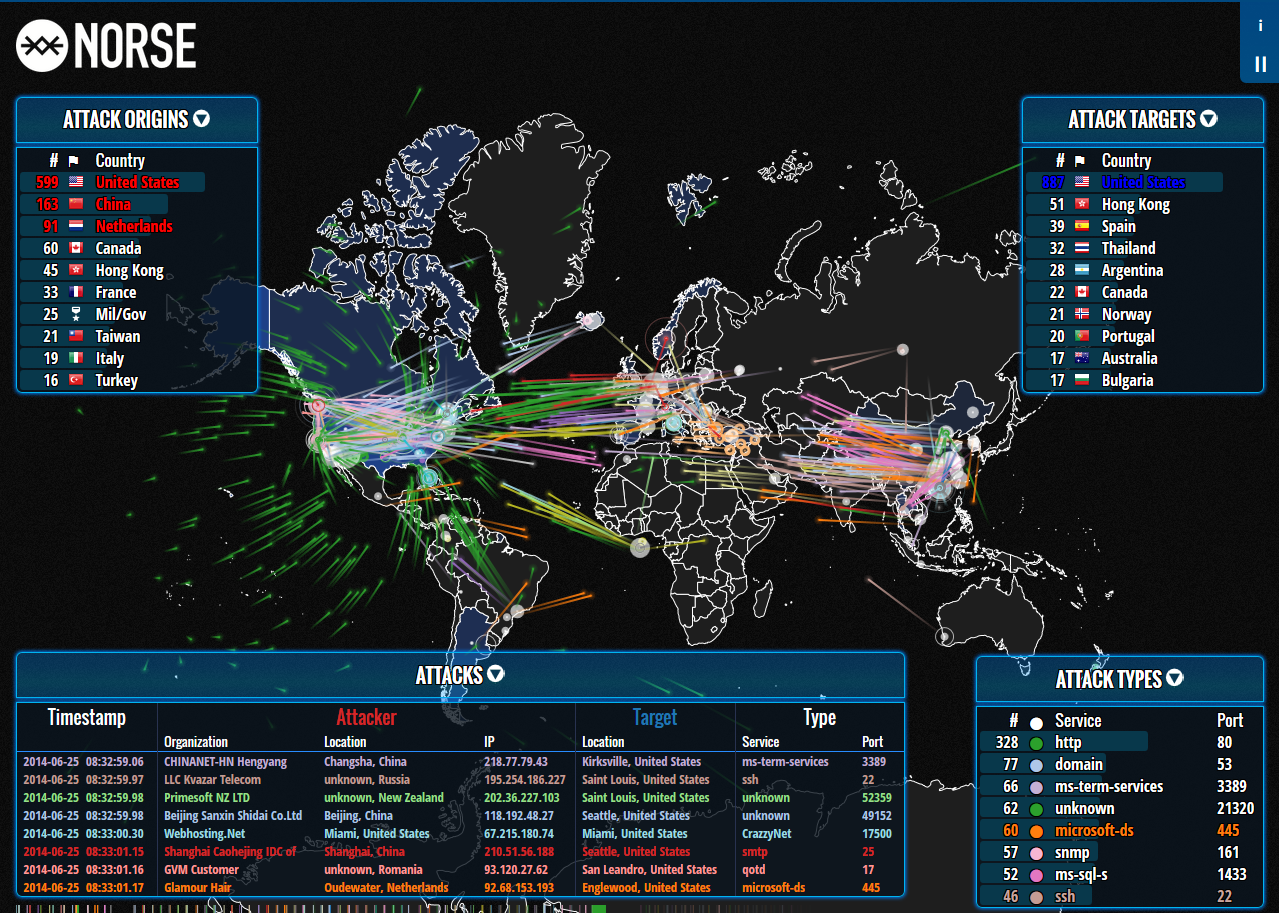
Problem Statement: Since the Onset of the third decade of this century, the world is witnessing the revival of direct confrontation at various potentially sensitive zones all over the globe. Among those, Ukraine and Israel are the two most prominent ones, as they drag major global stakeholders, often rivals, into their clout. Due to these have stakes, the above two zones, naturally offer fertile ground for conducting the proxy warfare among these stakeholders. Meanwhile, the nature of warfare is also evolving over the years and very rapidly shifting from conventional contact warfare to non-contact warfare, which involves cyberspace. At both Ukraine and Israel this phenomenon of cyber warfare is being witnessed where conflicting parties severed at proxies in multitude of engagements. This research focuses on drawing lessons for the border security from studying the affairs in Ukraine and Israel, and analyzing the developments from their position.
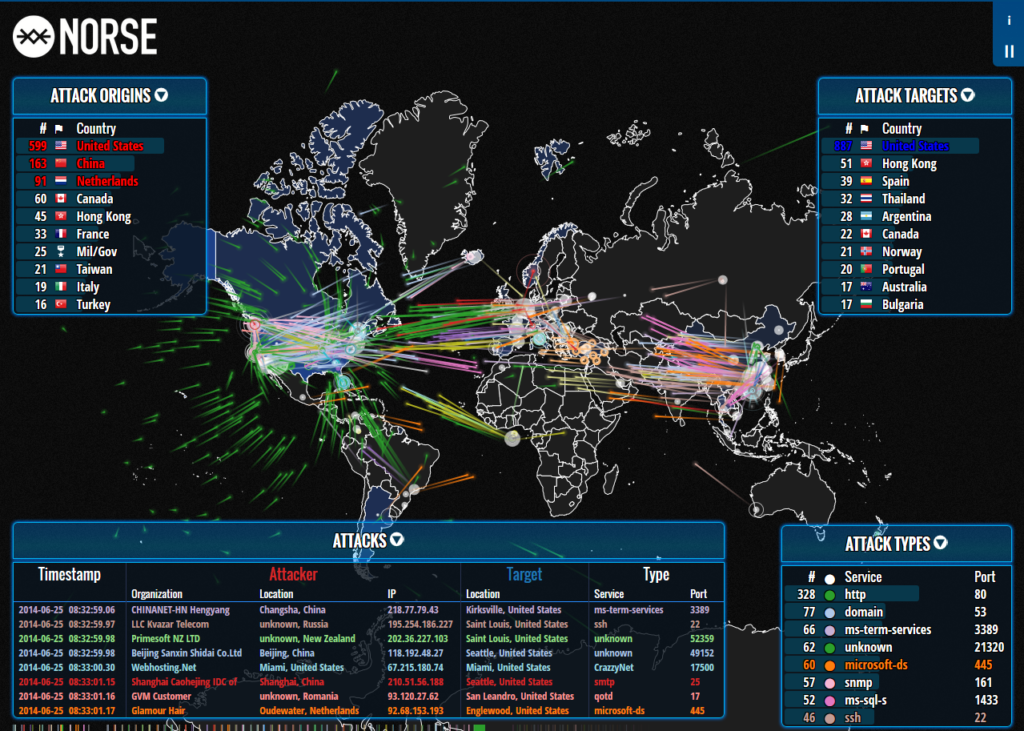
Aim of the Project: Drawing lessons from the Ukraine and Israel affairs by understanding the conduct of proxy warfare through cyberspace so that Bordermen could prepare accordingly to ensure Border Security.
Conceptual Framework:
The conceptual framework mainly focuses on five concepts: Proxies, Warfare, Compressive power and Cyberspace; and based on the above three ensuring the Border Security. Proxy in general sense refers to as ‘Acting on behalf of someone else’s interest’ also known as sponsor. Since the term got into prominence in the era of bipolarity, it is conceived that the proxy might involve two contradicting parties and serving on their behalf. For this research however, the concept is used to suit a different context where multitude of stakeholder are invested in an engagement. Therefore to the active parties, they would serve as allies, allies of enemy, neutrals and enemies of the neutrals. Warfare refers to the venture of subduing the opponent by diminishing its power, when done through proxy is called proxy warfare. The research however considers not just the hard military power, but the comprehensive power which involves other elements of statecrafts as well, such as Territory, People, Finance, Government, Infrastructure and Allies. Proxy warfare thus aims to diminish the comprehensive power for the purpose of this research. Cyberspace is a digital space for multitude of virtual activity. There are four fundamental elements of the cyberspace: User, Services, Communication Infrastructure, and Digital Assets. The research looks into their utilization in context of Proxy Warfare through Cyber space in diminishing the comprehensive power. In this background the border security not just concentrated on safeguarding the territorial border, but directly concerned with all the elements of comprehensive power.
Research Question:
What are the lessons for the border security from Ukraine and Israel Affairs in context of Proxy warfare through Cyberspace?
Research Methodology:
In perview of Border Security the research looks into three different domains Strategic, Tactical and Operational. The methodology employed gathers inputs from various web sources such a news outlets, articles, research work, and reports outlying the conduct of proxy warfare practices through cyber space that might be directed at diminishing the comprehensive power. Based on the outcome of those activities/practices that may vary between success and failure the inference would be made to draw lessons for the Border Security.
(Read More: Key takeaways from webinar on Safeguarding India’s Borders and Strengthening Cybersecurity)
Implications:
The lessons drawn from the affairs of Israel and Ukraine would provide useful insights to Bordermen, Policy makers and government institutions, which they could employ for strengthening the border security systems and mechanisms.



Leave a Reply